Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
This section illustrates how to manage people and their permissions, groups, and attributes in Immuta.
The how-to guides linked on this page illustrate how to register your users with Immuta.
Identity managers are used with Immuta to provide authentication and fine-grained user entitlement. This section provides reference and how-to guides for the identity managers that integrate with Immuta.
Immuta policies are dynamic and change for the user accessing data. Every user accessing policy-protected data must exist in Immuta, regardless of if they will interact with the Immuta UI. The guides in this section discuss managing users and their permissions, groups, and attributes.
This section includes a general guide for configuring an OpenID provider and guides for specific OpenID providers in Immuta. The getting started section below provides best practices for setup and configuration.
Start by creating a few initial subscription and data policies so that you know the user metadata you will need from your IAM. For example, will user attributes be used to author policies, or will groups also be needed? The subscription and data policies below illustrate the need for both groups and attributes to be imported from the IAM to enforce appropriate access controls:
Subscription policy: Allow all users in the Marketing group to access data sources tagged Marketing.
Data policy: Mask all columns tagged Location except for users with the attribute AccessLevel.Gold.
Validate that your provider is supported by Immuta and supports SCIM. If your provider is not listed or does not support SCIM, reach out to your Immuta representative for guidance.
Configure your OpenID provider in Immuta with SCIM enabled. Guides for specific providers are linked below.
Once your IAM is configured, complete one of the following tasks:
The how-to guides linked on this page illustrate how to register your users with Immuta.
See the guide for information on the best ways the keep your users in sync with Immuta with the least amount of effort. Use one of the options below to register your users in Immuta:
.
.
configured in Immuta allow users to authenticate using an existing identity management system and can optionally be used to synchronize user groups and attributes into Immuta.
.
.
.
.
.
.
Identity managers are used with Immuta to provide authentication and fine-grained user entitlement.
: Configure Okta with Immuta using LDAP to sync users to Immuta.
: Get started with OpenID Connect.
Okta with OpenID Connect: Configure Okta with Immuta using OpenID to sync users to Immuta.
OneLogin with OpenID Connect: Configure OneLogin to sync users to Immuta.
: Get started with SAML.
: Configure SAML IAM protocol to sync users to Immuta.
: Configure Microsoft Entra ID to sync users to Immuta.
: Configure Okta with Immuta using SAML to sync users to Immuta.
: This reference guide describes the options, support, and limitations when using IAMs to sync users into Immuta.
: This reference guide describes the logout processes using SAML 2.0 single logout protocol which allows identity providers to terminate sessions across a user's applications nearly simultaneously with a single logout request.
: This reference guide lists the configuration options for SAML SLO protocol.
This section includes a general guide for configuring a SAML provider and guides for specific SAML providers in Immuta. The getting started section below provides best practices for setup and configuration.
Start by creating a few initial subscription and data policies so that you know the user metadata you will need from your IAM. For example, will user attributes be used to author policies, or will groups also be needed? The subscription and data policies below illustrate the need for both groups and attributes to be imported from the IAM to enforce appropriate access controls:
Subscription policy: Allow all users in the Marketing group to access data sources tagged Marketing.
Data policy: Mask all columns tagged Location except for users with the attribute AccessLevel.Gold.
Validate that your provider is supported by Immuta and supports SCIM. If your provider is not listed or does not support SCIM, reach out to your Immuta representative for guidance.
Configure your SAML provider in Immuta with SCIM enabled. Guides for specific providers are linked below.
Once your IAM is configured, complete one of the following tasks:
Editing your IAM configuration
With the exception of the IAM ID (also called the display name), any of these settings can be changed after an IAM is configured. To edit IAM settings, click the dropdown arrow next to the IAM listed in the identity management section on the app settings page and then make your changes.
There are additional configuration options available for the SAML 2.0 protocol than are referenced in this guide, which only outlines the required settings. For details about the additional options, see the SAML protocol configuration options reference guide.
Navigate to the Immuta App Settings page.
Scroll to the Identity Management section and click Add IAM.
Complete the Display Name field and select SAML from the Identity Provider Type dropdown.
Take note of the ID and copy the SSO Callback URL to use as the ACS URL in your identity provider.
Adjust Default Permissions granted to users by selecting from the list in this dropdown menu.
Complete the Entry Point field. This is the location of your single sign on application that will be redirected to from the Immuta login page.
Upload your Signing Certificate. This is your identity provider's public signing certificate.
Opt to Enable SCIM support for SAML. Validate that the usernames in your IAM match those in your data platform (Snowflake, Databricks, etc.). If they are incorrect in the IAM or the casing doesn't match, fix the data platform username in the identity provider before configuring SCIM in Immuta.
In the Profile Schema section, map attributes in SAML to automatically fill in a user's Immuta profile. Note: Fields that you specify in this schema will not be editable by users within Immuta.
Click Test Connection and Test User Login.
Save your configuration.
An Immuta tenant with version 2020.4 or higher is required to use Immuta's SCIM 2.0 feature.
Users have to be an administrator in Okta to edit or add applications.
The following Okta provisioning features are supported by Immuta:
Import users from Okta: Okta users who had previously been assigned to an Okta application can be imported to your Immuta tenant.
Push users to Immuta: Okta users who are assigned to the Immuta application in Okta are automatically added as members to your Immuta tenant.
Deactivate users in Immuta: Okta users who are unassigned from the Immuta application in Okta or are deleted or deactivated from Okta are automatically deactivated in your Immuta tenant.
Push groups to Immuta: Groups and their members in Okta can be pushed to your Immuta tenant.
Remove groups from Immuta: Groups in Okta are removed from your Immuta tenant when they are no longer mapped to your Immuta application in Okta.
Map user attributes from Okta to Immuta: You can map user attributes between Okta and your Immuta tenant. The mapping will remain synced by detecting profile changes in Okta.
Log in to your Okta instance and click Applications in the menu in the left pane.
Click Browse App Catalog, and then search for and select Immuta.
Click Add.
In General Settings, opt to change the Application label. Then, click Next.
Click View Setup Instructions and complete the tutorial to configure the IAM in Immuta. Note: You will complete all steps outlined for the Immuta App Settings page except Test User Login. You cannot test the login or save the IAM configuration in Immuta until you have added yourself as a user to the application in Okta. These steps are outlined in the next section.
In the Okta console under Advanced Sign-on Settings, fill in the following fields.
Base URL (typically your Immuta tenant URL)
IAM ID (found on the Immuta App Settings page)
Click Done.
Attribute matching allows you to determine how to uniquely identify a user in Okta and match that user in Immuta at login and during provisioning. Immuta supports the following matching attributes in Okta:
Users:
id
userName
email
displayName
emails[type eq "work"].value
Groups
id
displayName
Using any other attribute in Okta as a matching attribute results in an error. See the Okta documentation for details about attribute matching and how to configure it.
Click the Assignments tab.
Click Assign and then Assign to People.
Enter your name in the search field to filter results, and then click Assign.
Click Save and Go Back, and then click Done.
Return to the Immuta console and click Test User Login. Once this test passes, click Save.
Navigate to the App Settings page in Immuta, and click the Add IAM button.
Complete the Display Name field and select SAML as your IAM type from the Identity Provider Type dropdown.
Adjust Default Permissions granted to users by selecting from the list in this dropdown menu, and then complete the required fields in the Client Options section.
Enable SCIM support for SAML by clicking the checkbox, which will generate a SCIM API Key. Validate that the usernames in your IAM match those in your data platform (Snowflake, Databricks, etc.). If they are incorrect in the IAM or the casing doesn't match, fix the data platform username in the identity provider before configuring SCIM in Immuta.
In the Profile Schema section, map attributes in SAML to automatically fill in a user's Immuta profile. Note: Fields that you specify in this schema will not be editable by users within Immuta.
Enable Sync groups from SAML to Immuta and Sync attributes from SAML to Immuta by selecting the checkboxes, and then click the Test Connection button.
Once the connection is successful, click the Test User Login button.
Before you save the configuration, store the SCIM information that displays on the Immuta App Settings page, as it will be used in subsequent steps.
In Okta, navigate to your application and click the Provisioning tab.
Click Configure API Integration and then select the Enable API integration checkbox.
Fill in the following fields:
Base URL (found on the Immuta App Settings page as SCIM URL)
API Token (found on the Immuta App Settings page as SCIM Api Key)
Click Test API Credentials.
Once that test passes, click Save.
You will automatically navigate to the Provisioning tab. To make sure everything syncs as expected, select To App in the Settings pane, click Edit, and enable the following fields:
Create Users
Update User Attributes
Deactivate Users
Click Save.
Syncing current users in Okta
Once SCIM is enabled in Okta, it only works for changes in Okta going forward. To get your current users to sync, navigate to the Assignment tab and click Provision User in Okta. Existing users (or any new users you add/remove) should now display in Immuta under this external IAM.
Using the same group to assign users to Okta (groups added to the Okta Assignments tab) and to push groups and users to Immuta (groups added to the Okta Push Groups tab) is not supported. See the Okta troubleshooting guide for details.
The Okta directory cannot be synced with Immuta's internal IAM (BIM). You must configure an external IAM in Immuta to push users and groups from Okta to Immuta.
You should create a new Immuta IAM and a new Okta application for Immuta to set up the provisioning. An existing setup can cause discrepancies between the Okta directory and the app, leading to syncing failures.
When making a GET request for a user, there are extra attributes in the response.
Add users in Okta SCIM
Navigate to your application in Okta and click the Assignments tab.
Click Assign and then Assign to People.
Enter the name of the user you would like to add in the search field and click Assign.
Click Save and Go Back, and then click Done.
The user has been added to your application in Okta and displays as a user in Immuta under this external IAM.
Remove users from Okta SCIM
Click the delete icon next to the user you want to remove.
When prompted to make sure you want to delete this user, click OK.
This user is removed from your application in Okta and displays as disabled in Immuta under this external IAM.
Group sync
Groups will automatically sync in Immuta for any users added to the SCIM application if
Push Groups in Okta is enabled
Sync Groups is enabled in Immuta
Add users to groups
In Okta, navigate to your application and click on the Assignments tab.
Click on the name of the user whose groups you want to update.
Click on the Groups tab.
To add a new group, start to type the name of an existing group in the search field, and when it displays, click Add.
This group has been added to the user in Okta. It will also automatically appear in Immuta for the same user.
Remove users from groups
In Okta, navigate to your application and click the Assignments tab.
Click the name of the user whose groups you want to update, and then navigate to the Groups tab.
Click the delete icon next to the group you want to remove for this user.
This group has been removed from the user in Okta, and it will automatically be removed from this user in Immuta.
Add attributes to users
In Okta, navigate to your application and click To App on the Provisioning tab.
Click the Go to Profile Editor button.
Click Add Attribute and fill in the following fields:
Data type (defaults to string).
Display name.
Variable name.
External namespace. This field has to be formatted using a special schema format (e.g., urn:ietf:params:scim:schemas:extension:enterprise:2.0:DEMOEXT). Copy this information; you will need it for Immuta configuration.
Click Save.
By default, the value for this attribute is empty. Follow the Adding Attribute Values section to add values.
Update the SCIM attribute schema in Immuta
In Immuta, navigate to the App Settings page and edit your SCIM configuration.
Scroll to the Attribute Schema section under Sync Attributes.
Click Add Attribute and complete the following fields:
SCIM Schema: <found on the Okta SCIM attribute page (in the previous section)>
IAM Immuta Attribute Prefix: this can be anything you want
Click Test Connection and then Test User.
Save your changes.
Add attribute values
After adding attributes to users and updating the SCIM Attribute Schema in Immuta,
In Okta, navigate to the Assignments tab for your application and click the edit icon next to the user you want to update attributes for.
Scroll to the attribute you created and add a value in the textbox.
Save your changes.
Now that this attribute has been added to the user in Okta, it will automatically appear in Immuta for the same user.
You must configure a SCIM application and enable sync attributes before syncing external usernames.
In Immuta, navigate to your Okta SCIM configuration on the App Settings page.
Under Sync attributes from SAML to Immuta, add an attribute for the field you would like to map to an external username.
Copy and paste the resulting attribute for the desired external username.
Click Test Connection and then Test User.
Save your changes.
The SAML 2.0 single logout (SAML SLO) protocol allows identity providers to terminate sessions across a user's applications nearly simultaneously with a single logout request.
SAML SLO enabled in Immuta can minimize security risks by terminating abandoned sessions after a timeout event occurs or after a user logs out of their identity provider or another application. Once users are logged out of Immuta, they must re-authenticate to log back in.
Immuta APPLICATION_ADMIN permission
An identity provider that supports the SAML protocol. See this list of supported identity providers and their protocols.
There are two logout processes for SAML SLO:
Application-initiated logout: A user logs out from a service provider.
Identity-provider-initiated logout: A user logs out from their identity provider.
The following objects are referenced in both processes below:
Principal: A user, service, or process that must authenticate with a service before being granted access and privileges.
Service provider (or session participant): The service or application the principal wants to be granted access to (for example, Immuta).
Session authority (or identity management provider): The identity management provider that verifies the principal's identity. See this list of supported identity providers for examples.
Session: The period during which the principal is authenticated with the service provider; a session is started when a user authenticates their identity using a password or another authentication protocol and the service provider has verified that the user is allowed access to their service.
1. The principal requests to log out of the service provider, or a timeout event initiates a logout request.
1. User logs out of Immuta.
2. The service provider sends a logout request to the session authority.
2. Immuta sends a logout request to Okta and terminates the user's Immuta session.
3. The session authority validates the signature and data in the request and sends a logout request to all the service providers for the current authenticated session (except the service provider from which the logout was initiated).
3. Okta validates the signature and data in the request and sends a logout request to all the other applications the user is logged in to.
4. The service providers terminate the sessions and send logout responses to the session authority indicating that the users has been logged out.
4. The other applications validate the signature and the data in the request and terminate the user's sessions in their application.
5. The session authority ends its own session with the principal.
5. Okta terminates its own session with the user.
6. The session authority sends a logout response message to the service provider from which the logout was initiated.
6. Okta sends a logout response message to Immuta.
1. The principal requests to log out of the session authority, or a timeout event initiates a logout request.
1. User logs out of Okta.
2. The session authority validates the signature and data in the request and sends a logout request message to all the service providers for the current authenticated session.
2. Okta validates the signature and data in the request and sends a logout request to all applications the user is logged in to.
3. The service providers validate the signature and data in the request and terminate the sessions.
3. Immuta and other applications validate the signature and data in the request and terminate the user's sessions.
4. The service providers terminate the sessions and send logout responses to the session authority indicating that the users has been logged out.
4. Immuta and other applications send a logout response to Okta to indicate the user has been logged out.
5. The session authority ends its own session with the principal.
5. Okta terminates its own session with the user.
Immuta's SAML SLO support has been tested with the following identity providers:
Key Cloak
Microsoft Entra ID
See your identity provider's documentation to determine whether or not your provider supports SAML SLO. For a list of identity providers and protocols supported by Immuta, see the identity management support matrix.
Immuta cannot ensure that other service providers will log out, as Immuta has no control over those applications.
Navigate to the App Settings page in the Immuta console and click the Add IAM button.
Complete the Display Name field and select OpenID from the Identity Provider Type dropdown.
Adjust Default Permissions granted to users by selecting from the list in this dropdown menu.
Navigate to OneLogin, click Administration, and then select Applications from the Applications menu.
Click Add App in the top right corner of the screen. Search for and select OpenID Connect (OIDC).
Complete the Display Name field and click Save.
From the Identity and Access Management window in your Immuta tenant, copy the SSO Callback URL to your clipboard.
Return to OneLogin, click the Configuration tab in the left panel, and paste the URL in the Login Url and Redirect URI's fields.
Click Save in the top right corner of this screen.
Click the SSO tab in the left panel of your OneLogin account. Copy the Client ID and the Client Secret and paste these values in the corresponding fields in your Immuta tenant.
Then, right click the Well-known Configuration text from the SSO tab of OneLogin, and copy the link to your clipboard.
Return to your Immuta tenant, and paste this link in the Discover URL field; pasting this link here prevents you from having to manually fill out the rest of the form.
Confirm email as the User ID claim, and fill out the Scopes section.
Return to OneLogin and scroll to the Token Endpoint section. Select POST from the Authentication Method dropdown.
Click Save.
Return to your Immuta console, opt to Enable SSL and Enable SCIM support for OpenID. Validate that the usernames in your IAM match those in your data platform (Snowflake, Databricks, etc.). If they are incorrect in the IAM or the casing doesn't match, fix the data platform username in the identity provider before configuring SCIM in Immuta.
In the Profile Schema section, map attributes in OpenID to automatically fill in a user's Immuta profile. Note: Fields that you specify in this schema will not be editable by users within Immuta.
Opt to Allow Identity Provider Initiated Single Sign On, External Groups and Attributes Endpoint, and Migrate Users.
Click Test Connection. Once the connection is successful, click Test User Login.
Click Save.
Okta LDAP Interface is a built-in Okta integration that enables you to expose your Okta directory over standard LDAP wire. The Okta LDAP Interface exposes the entire Okta directory.
The LDAP interface is not an isolated application
This means that you cannot manage the assignment of users and groups to the LDAP Interface the same way you would in a web application. Instead, you should be able to leverage LDAP filters to moderate access to applications that call the LDAP Interface (i.e., filtering user attributes and groups.)
Go to the Admin Console in your Okta account.
Select Directory, and then click Directory Integrations.
Select Add Directory and Add LDAP Interface. You will be presented with the details required to make a successful LDAP connection.
Create a service account
Create a service account to use as your LDAP bind user; any Okta admin with the "view users" permission can serve the role. Choose the Read-Only Admin to grant the least privilege.
Navigate to the App Settings page in Immuta.
Click the Add IAM button.
Complete the Display Name field and select LDAP/Active Directory from the Identity Provider Type dropdown.
Adjust Default Permissions granted to users by selecting from the list in this dropdown menu, and then complete the required fields in the Credentials and Options sections. Note: Either User Attribute OR User Search Filter is required, not both. Completing one of these fields disables the other.
Opt to have Case-insensitive user names by clicking the checkbox.
Opt to Enable Debug Logging or Enable SSL by clicking the checkboxes.
In the Profile Schema section, map attributes in LDAP/Active Directory to automatically fill in a user's Immuta profile. Note: Fields that you specify in this schema will not be editable by users within Immuta.
Opt to enable the following settings by selecting their checkboxes:
Enable scheduled LDAP Sync support for LDAP/Active Directory
Require manual approval before a user can use Immuta
Enable pagination for LDAP Sync: Once enabled, confirm the sync schedule written in Cron rule; the default is every hour. Confirm the LDAP page size for pagination; the default is 1,000.
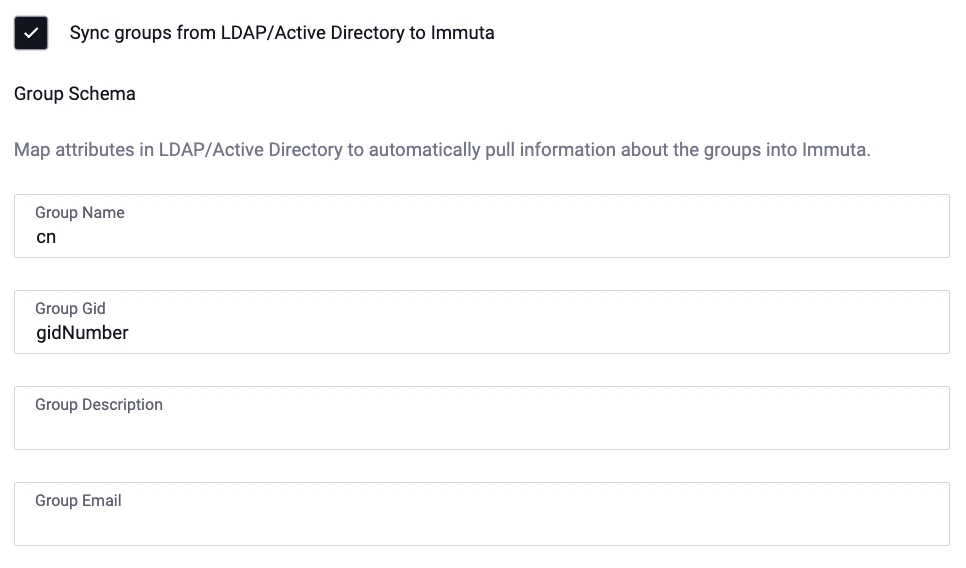
Sync groups from LDAP/Active Directory to Immuta: Once enabled, map attributes in LDAP/Active Directory to automatically pull information about the groups into Immuta.
Sync attributes from LDAP/Active Directory to Immuta: Once enabled, add attribute mappings in the attribute schema. The desired attribute prefix should be mapped to the relevant schema URN.
External Groups and Attributes Endpoint
Make Default IAM
Migrate Users from another IAM
Click the Test Connection button.
Once the connection is successful, click the Test User Login button.
Click the Test LDAP Sync button if scheduled sync has been enabled.
Click Save and confirm your changes.
To enforce directory-wide MFA, create an authentication policy in Okta (if you do not yet have MFA policies in place).
Navigate to Security in the Okta Admin console.
Select Authentication, and then click Sign On.
Note: If you enforce MFA on the user that’s configured as your LDAP bind user, the integration won’t work. You will therefore need to make that user exempt in your MFA policies.
Editing your IAM configuration
With the exception of the IAM ID (also called the display name), any of these settings can be changed after an IAM is configured. To edit IAM settings, click the dropdown arrow next to the IAM listed in the identity management section on the app settings page and then make your changes.
Navigate to the Immuta App Settings page.
Scroll to the Identity Management section and click Add IAM.
Complete the Display Name field and select OpenID from the Identity Provider Type dropdown.
Take note of the ID and copy the SSO Callback URL to use as the ACS URL in your identity provider.
Adjust Default Permissions granted to users by selecting from the list in this dropdown menu.
Enter the Client ID and Client Secret from your identity provider.
Enter the URL of your identity provider's discovery endpoint in the Discover URL field. If you do not provide this URL, you will have to complete the manual endpoint specification fields (authorization endpoint, issuer, token endpoint, etc.).
Opt to add additional Scopes.
Opt to Enable SCIM support for OpenID by clicking the checkbox, which will generate a SCIM API Key. Validate that the usernames in your IAM match those in your data platform (Snowflake, Databricks, etc.). If they are incorrect in the IAM or the casing doesn't match, fix the data platform username in the identity provider before configuring SCIM in Immuta.
In the Profile Schema section, map attributes in OpenID to automatically fill in a user's Immuta profile. Note: Fields that you specify in this schema will not be editable by users within Immuta.
Opt to Allow Identity Provider Initiated Single Sign On to use the IDP-Initiated SSO feature by selecting the checkbox.
Opt to Migrate Users from another IAM by selecting the checkbox.
Click Test Connection and Test User Login.
Save your configuration.
Identity managers are used with Immuta to provide authentication and fine-grained user entitlement. A number of identity managers can be configured and enabled in Immuta, each with a specific set of configuration options that enable Immuta to communicate with the IAM system and map the users, permissions, groups, and attributes into Immuta.
The Immuta IAM can be used as a complete solution for authentication and authorization. Group and attribute values within the Immuta IAM can be used to broker access to projects and data sources and to create policies.
The Immuta IAM is enabled by default, so there are no additional configuration options needed to support this mode.
External identity managers configured in Immuta allow users to authenticate using an existing identity management system and can optionally be used to synchronize user groups and attributes into Immuta. The synchronization between Immuta and your external IAM is one-way: changes made to your users' entitlements or users added in Immuta will not be reflected in your external IAM. Each identity manager configured in Immuta is assigned a unique identifier, referred to as the IAM ID, and all users, groups, and attributes are associated with exactly one IAM ID.
The table below illustrates the features supported by each IAM protocol.
Read user groups on user login
Yes
Yes
No - it needs an external user info service.
Read user attributes on user login
Yes
Yes
No - it needs an external user info service.
Provisioning: SCIM 2.0 Support (users & groups)
No
Yes
Yes
Provisioning: Periodic directory sync (users & groups)
Yes
No
No
Read ALL directory groups for policy authoring
Yes
Yes, with SCIM.
Yes, with SCIM.
Consume attributes/groups from arbitrary sources
Yes, with a shim.
Yes, with a shim and only if NOT using SCIM.
Yes, with a shim and only if NOT using SCIM.
The table below illustrates common providers that support the protocols listed above. However, this list may not be all-inclusive, and if a provider stops supporting a protocol, Immuta may not fully support that provider.
Active Directory
Yes
No
No
No
ADFS This provider only supports authentication with integrations, meaning users can authenticate to their integration, but their attributes will not be synced; attributes will only be synced when users authenticate with the Immuta UI.
No
Yes
Yes
No
Amazon Cognito This provider only supports authentication with integrations, meaning users can authenticate to their integration, but their attributes will not be synced; attributes will only be synced when users authenticate with the Immuta UI.
No
No
Yes
No
Centrify
Yes
Yes
Yes
No
JumpCloud
Yes
Yes
Yes
No
Keycloak This provider only supports authentication with integrations, meaning users can authenticate to their integration, but their attributes will not be synced; attributes will only be synced when users authenticate with the Immuta UI.
No
Yes
Yes
No
Microsoft Entra ID
No
Yes
Yes
Yes
Okta
Yes
Yes
Yes
Yes
OneLogin
Yes
Yes
Yes
Yes
OpenLDAP & other LDAP servers
Yes
No
No
No
Oracle Access Manager
No
Yes
Yes
Yes
Ping Identity
Yes
Yes
Yes
Yes
Identity managers are added from the app settings page. Settings like default permissions, profile schema, group schema, group permissions, and external groups and attributes endpoint are managed from that page as well.
Each identity manager supports the configuration of default permissions. This configuration setting controls what permissions each user who logs in receives by default. These permissions are applied the first time each user logs in, and any changes to the default permissions will only apply to new users.
In the case where the default permissions are empty, new users receive no special permissions in Immuta and an administrator will need to grant them any permissions that they need. Alternatively, group permissions may be configured, in which case permissions will be evaluated based on the groups users belong to.
On the app settings page, application admins can migrate user accounts from one identity manager configured in Immuta to another.
Once this setting is enabled, Immuta checks user IDs when users log in against the IAM they are migrating from, so the user IDs for these accounts must match. (For example, if their userID in Immuta's built-in IAM is consumer@example.com, their user ID in the new IAM should be consumer@example.com.) Then, users' profiles will be moved to the new IAM, including their subscriptions, permissions, and pending requests.
If a user does not have an exact user ID match, a user admin can manually migrate their account.
Sync attributes and groups
When enabling SCIM, it is best to enable sync attributes and groups. If this is not done, the IAM performing provisioning will likely continue to try to perform updates that are otherwise blocked.
When configuring a SAML or OpenID IAM, application admins can enable SCIM support, which allows these IAMs to automatically create new users in Immuta and keep existing users up-to-date. Once enabled, the majority of the profile schema fields will be hidden and automatically synced from the SCIM response. The API key will be displayed to be used to configure provisioning in the external IAM. After the configuration is saved, it will be hashed. A new key can be regenerated here if the old key is ever lost.
If SCIM support is not enabled in a SAML configuration, administrators must disable relevant users in Immuta if they are removed from the IAM, since the IAM will not send Immuta those updates.
SCIM and Azure
In some instances, updates in Azure are instantly pushed to Immuta. In others, however, pushes update on a schedule (roughly every 40 minutes), and there is more than one sync event (i.e., users may be updated in the first event and user memberships in another).
SCIM will skip updates and will not inform Immuta that an attribute should be removed from a user in the following scenarios, even if the attribute mapping has been deleted from the IAM configuration on the Immuta app settings page:
Attribute is set to empty (removed) in Microsoft Entra ID
Attribute is deleted in Microsoft Entra ID
In both of these scenarios, Azure doesn’t send Immuta a payload to remove the attribute, as it considers the action a redundant export. As a result, the attribute values that previously existed in Microsoft Entra ID will not get removed from the user in Immuta.
To remediate this limitation, take one of the following actions:
Change the attribute to a non-impacting value other than empty in Microsoft Entra ID.
Alternatively, remove the attribute mapping from the attribute schema section of the IAM configuration on the Immuta app settings page. Then, trigger an update for that user in Microsoft Entra ID by making a change to any value for that user. Microsoft Entra ID will send an update for that user to Immuta, and Immuta will remove the attribute from the user. Note that if that attribute mapping is ever re-added in Immuta on the app settings page, that attribute will be added to the user again.
See Known issues for provisioning in Microsoft Entra ID for more details about this limitation.
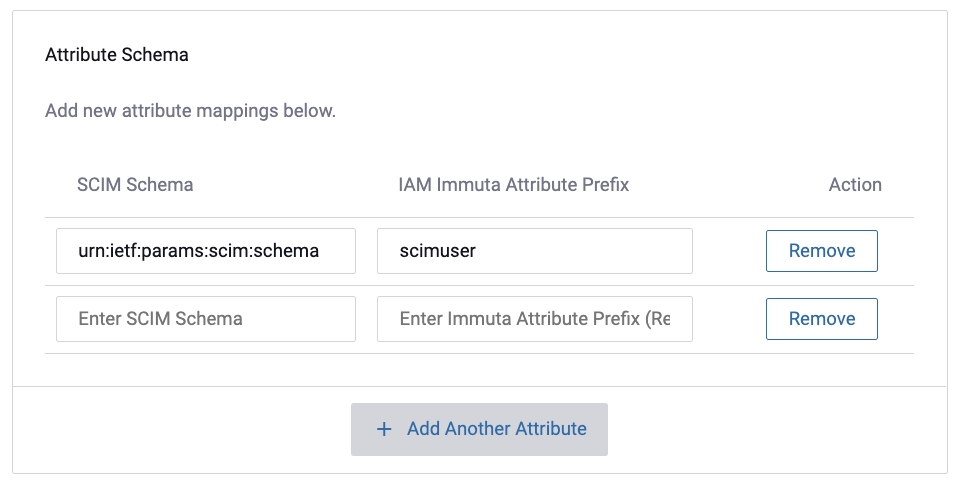
Attribute mapping for SCIM is slightly different compared to the normal attribute mapping for IAMs. For SCIM mapping, the desired attribute prefix should be mapped to the relevant schema URN:
In Immuta this attribute would translate from SCIM Schema Attribute: “urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:Test” into Immuta Attribute: “scimuser.Test”
LDAP sync takes an existing and configured LDAP IAM and seeds Immuta with all of its users, subject to the intersection of the IAM's user search filter and the plugin's user search filter. When configuring an LDAP/Active Directory IAM , application admins can enable scheduled LDAP sync; this will allow directory users to be registered within Immuta without the users having to log directly into Immuta.
Once enabled, LDAP sync will automatically provision and sync users from LDAP on an approved schedule. The default is every hour, but can be adjusted to an organization's needs.
Application admins can also enable pagination for LDAP sync, which will be a predetermined page size when searching LDAP during this scheduled sync.
Each identity manager configured has a mapping of attributes from the source system into attributes on the user profile in Immuta.
Profile schema attributes provide general purpose user information and cannot be used as entitlements for policies.
Identity managers that support group synchronization will have a group schema configuration option. This defines how group attributes are mapped in Immuta.
This example is the group schema mapping for an LDAP/Active Directory IAM.
When an identity manager is configured to synchronize groups you will have the option to define a mapping of groups to Immuta permissions. Users who belong to one of the given groups will be granted the listed permissions automatically. Additionally, user admins can add attributes in Immuta to groups from external IAMs.
An IAM system can be used for authentication and combined with an external REST endpoint to retrieve user groups and attributes. This option provides flexibility in exactly how groups and attributes are associated with users in Immuta.
Immuta does not support adding duplicate external usernames from different IAMs in a single Immuta tenant. If duplicate external usernames from different IAMs are registered in Immuta and mapped to one or more users, those users will receive an error like the following when they attempt to query Immuta-protected data: Single-row subquery returns more than one row.
Administrator account in Okta.
Immuta's OpenID Connect integration supports the following features
Service Provider (SP)-Initiated Authentication (SSO) Flow
Identity Provider (IDP)-Initiated Authentication (SSO) Flow
Log in to Okta as an Admin, navigate to the Applications tab, and click Add Application.
Search for Immuta in the search bar and click Add.
Choose a name for your integration and click Next. Then select the OpenID Connect button.
Scroll down and enter the Base URL for your Immuta tenant.
Enter the IAM ID for your Immuta OIDC integration (if you have not created an IAM ID, you will complete that step in the next section).
Click Done and once the page reloads, navigate back to the Sign On tab and copy down the Client ID and Client secret.
Attribute matching allows you to determine how to uniquely identify a user in Okta and match that user in Immuta during login and provisioning. Immuta supports the following matching attributes in Okta:
Users:
id
userName
email
displayName
emails[type eq "work"].value
Groups
id
displayName
Using any other attribute in Okta as a matching attribute results in an error. See the Okta documentation for details about attribute matching and how to configure it.
Log in to Immuta and click the App Settings icon in the left sidebar.
Click the Add IAM button and enter a Display Name.
Select OpenID from the Identity Provider Type dropdown menu.
If required, navigate back to Okta and enter the IAM ID below the Base URL then complete the steps from the Okta section.
In the Identity Management section of the Immuta console, enter the Client ID and Client Secret you copied from Okta in the previous section.
Enter the following URL in the Discover URL field: https://<your_okta_workspace.com>/.well-known/openid-configuration.
Opt to add additional Scopes.
Opt to Enable SCIM support for OpenID by clicking the checkbox, which will generate a SCIM API Key. Validate that the usernames in your IAM match those in your data platform (Snowflake, Databricks, etc.). If they are incorrect in the IAM or the casing doesn't match, fix the data platform username in the identity provider before configuring SCIM in Immuta.
In the Profile Schema section, map attributes in OpenID to automatically fill in a user's Immuta profile. Note: Fields that you specify in this schema will not be editable by users within Immuta.
Opt to Allow Identity Provider Initiated Single Sign On to use the IDP-Initiated SSO feature by selecting the checkbox.
Opt to Migrate Users from another IAM by selecting the checkbox.
Click the Test Connection button.
Once the connection is successful, click the Test User Login button.
Click Save.
Immuta can integrate with Microsoft Entra ID as an IAM over SAML 2.0. This page outlines how to register Immuta as an Azure Enterprise Application with Single Sign-On over SAML 2.0.
Microsoft Azure subscription: Microsoft Azure requires a Premium subscription to create a non-gallery application, which is essential for this integration.
In the Microsoft Azure portal, browse to Enterprise Applications.
Click the New Application button and then select Create your own application.
Name the application with the name of your choice, select Integrate any other application you don't find in the gallery (Non-gallery), and click Create.
On the left menu, choose the Single sign-on menu item and then pick the SAML tile.
In the first section (Basic SAML Configuration), click the Edit icon and fill in Identifier (Entity ID) field with the full URI of your Immuta app (e.g., https://immuta.my-comany.com).
In the second section (User Attributes & Claims), specify the unique user identifier you want to use in Immuta. Common choices are the mail claim or the userprincipalname claim. You can also specify the user claims you want Azure to expose to Immuta. You will use the names of those claims to map them to Immuta user attributes when you .
In the third section (SAML Signing Certificate), click the Download link next to Certificate (Base64) and save the file on your hard drive:
In the fourth section, copy the Login URL and save it for when you will through the Immuta UI.
Now that you have an enterprise application in place, continue to create and configure an IAM in Immuta. You will need a few details from the Immuta UI to complete the configuration of the enterprise application.
Attribute matching allows you to determine how to uniquely identify a user in Microsoft Entra ID and match that user in Immuta at login and during provisioning. Immuta supports the following matching attributes in Microsoft Entra ID:
Users:
id
userName
email
displayName
emails[type eq "work"].value
Groups
id
displayName (See the below for group names.)
In Immuta, browse to App Settings, go to the Identity Managers section, and click Add IAM
Assign a name to the new IAM. Immuta will automatically derive the ID of the IAM from the name you pick.
Select SAML in the Identity Provider Type drop-down.
Start configuring the new IAM:
Default Permissions: The default permission that should be assigned to a Microsoft Entra ID user in Immuta.
Issuer: This field needs to have the same value as the Identifier (Entity ID) of the enterprise application (e.g., https://immuta.my-comany.com).
Entry Point: Paste the Login URL that you obtained in the previous section.
User ID Attribute: This field is the attribute that will contain the username of the user logging in.
Signing Certificate: Upload the certificate file you have previously downloaded and converted into a PEM encoded certificate.
Decryption Private Key: This field is the optional key for decrypting attribute assertions.
Enable SCIM support for SAML: Opt to enable SCIM support. Validate that the usernames in your IAM match those in your data platform (Snowflake, Databricks, etc.). If they are incorrect in the IAM or the casing doesn't match, fix the data platform username in the identity provider before configuring SCIM in Immuta.
Profile Schema: Map attributes in SAML to automatically fill in a user's Immuta profile. Note: Fields that you specify in this schema will not be editable by users within Immuta.
Enable any optional settings:
Link SQL
Allow Identity Provider Initiated Single Sign On: After checking this option, set disableRequestedAuthnContext to true under Additional Config Parameters.
Sync groups from SAML to Immuta
Sync attributes from SAML to Immuta: After selecting this checkbox, map your Entra ID attributes to Immuta in the Attribute Schema section.
External Groups and Attributes Endpoint
Before you can test the integration and save the new IAM, you will need to go back to the Microsoft Azure Portal and fill in the Reply URL.
In the Single sign-on page of your enterprise application, edit the first section with the title Basic SAML Configuration.
Fill in the Reply URL (Assertion Consumer Service URL) field with a value that adheres to the following format: ${IMMUTA_URL}/bim/iam/${IAM_ID}/user/authenticate/callback. For example, if the URL to your Immuta tenant is https://immuta.my-comany.com and the assigned IAM ID is MicrosoftEntraID, the value of the Reply URL field should be https://immuta.my-comany.com/bim/iam/MicrosoftEntraID/user/authenticate/callback. To save the changes, click Save. You can find the IAM ID that Immuta has assigned to the IAM in the form.
You should now be able to test the IAM and save it. After clicking Test Connection and letting Immuta hit the enterprise application URL, you will need to verify that the authentication flow works before you can save and create the IAM. To do so, click Test User Login and follow the instructions.
Save the changes in Immuta.
SCIM will skip updates and will not inform Immuta that an attribute should be removed from a user in the following scenarios, even if the attribute mapping has been deleted from the IAM configuration on the Immuta app settings page:
Attribute is set to empty (removed) in Microsoft Entra ID
Attribute is deleted in Microsoft Entra ID
In both of these scenarios, Azure doesn’t send Immuta a payload to remove the attribute, as it considers the action a redundant export. As a result, the attribute values that previously existed in Microsoft Entra ID will not get removed from the user in Immuta.
To remediate this limitation, take one of the following actions:
Change the attribute to a non-impacting value other than empty in Microsoft Entra ID.
Group names containing " are unsupported in the Microsoft Entra ID integration.
Immuta can consume user attributes from an external HTTP endpoint in an out-of-band fashion. This feature allows you to retrieve users' groups and authorizations from an additional resource, alongside the user attributes retrieved in the authentication flow. Such an external endpoint can be configured on any of the Identity Provider types that Immuta supports.
The following section instructs how to implement the HTTP service.
The service can authenticate requests with both or either of the following methods:
Basic username and password Authorization header
SSL cert validation
For more information, refer to .
Note: Immuta will expect non 200 error codes when the user info cannot be retrieved.
The user info endpoint will be called each time Immuta needs to synchronize with a remote IAM on user groups and authorizations. Immuta will query the endpoint with the user ID specified in request's query.
Note: The endpoint's path does not necessarily have to be /user-info.
Parameters
Responses
Response schema
Below is an example value that could be returned by the endpoint:
Click the App Settings icon in the left sidebar.
If you are modifying an existing IAM, click the name of the IAM. If you are creating a new IAM, click Add IAM.
At the very bottom of the IAM section, check the External Groups and Authorizations Endpoint checkbox.
In the External User Info URI field, enter the full path to your customer HTTP endpoint.
Optionally, check the Use Authentication checkbox and provide the username and password with which Immuta should authenticate when querying the user info endpoint. Immuta will subsequently send requests to the service with a Basic authorization header.
Optionally, enable SSL by checking the Enable SSL checkbox.
Optionally, if SSL is enabled, check the Require SSL Request Cert if your service requires SSL certificate validation. This step will require that you upload three files:
The SSL key file (*.pem)
The SSL cert file (*.pem)
The SSL CA file (*.pem)
Identity access management best practice: Organize user attributes and groups in Immuta and then transfer them to your IAM.
Note: User Admins can add attributes in Immuta to external IAM groups using the Add Attributes button.
Attributes can be added to individual users or groups and then included in and to restrict what data users can see. They can be created by a User Admin in the Immuta UI or mapped in from an .
To learn how to add attributes to a user or group, navigate to the .
Individual users are added into groups, and then groups are used in and to restrict what data users in each group can see. Groups are also used in assigning members to . Users can belong to any number of groups and can be added or removed from groups at any time.
To learn how to create a group, navigate to the .
External IDs for integrations can be mapped in for Snowflake, Databricks, Starburst (Trino), Redshift, Azure Synapse Analytics, and HDFS based on attributes from an external IAM system, allowing you to link an external account to the corresponding Immuta account even when usernames do not match between Immuta and the external system.
External IDs for integrations can be mapped in for Snowflake, Databricks, Starburst (Trino), Redshift, Azure Synapse Analytics, and HDFS based on attributes from an external IAM system.
Click the App Settings icon in the left sidebar and click Identity Management.
After you have clicked Add IAM, define the mapping in the Profile Schema section. Note: Mappings can also be disabled on the App Settings page, so it’s possible that not all of these fields will be available.
Click Save.
Test a login to ensure that the values are picked up correctly.
For IAMs where no mapping has been defined (including Immuta's built-in IAM), the external user ID mappings can be set manually.
Click the People icon and select the Users tab.
Select the user you want to edit.
In the Usernames section, click Edit for the technology username you want to change.
Complete the Username field in the modal that appears and click Save.
For Databricks usernames,
Select Databricks Username to map the Databricks username to the Immuta user and enter the Databricks username in the field. Username mapping for Databricks is case insensitive.
Select Unset (fallback to Immuta username) to use the Immuta username as the assumed Databricks username. Use this option if the user's Databricks username matches the user's Immuta username. Username mapping for Databricks is case insensitive.
Select None (user does not exist in Databricks) if this is an Immuta-only user. This option will improve performance for Immuta users who do not have a mapping to Databricks users and will be automatically selected by Immuta if an Immuta user is not found in Databricks. To ensure your Databricks users have policies correctly applied, manually map their usernames using the first option above.
For S3 usernames, use the dropdown menu to select the User Type. Then complete the S3 field. When selecting Unset (fallback to Immuta username), the S3 username is assumed to be the same as the Immuta username. User and role names are case-sensitive. See the for details.
All external IDs are displayed on the user details page and their user profile.
Click the People icon and select the Groups tab.
Click the New Group button.
In the modal, enter the new group's name. You can opt to enter a description of and email address for the new group.
Click Save.
Click the People icon and select the Groups tab.
Select the group you want to edit and select the Settings tab.
Click the Add Members button.
Begin typing in the Search by Member Name or Email text box.
Click on the name from the dropdown list to add this user to the group.
Authentication best practice: Use an for authentication and Immuta's internal IAM to manage attributes.
Click the People icon and select the Groups tab.
Select the group you want to edit and select the Settings tab.
Click Add Attributes.
Begin typing the attribute name in the Attribute text box.
If the attribute already exists, select it from the dropdown list.
If the attribute does not exist yet, enter the full name of the attribute, and then select it from the dropdown.
In the Attribute Value text box, enter a value.
If the value already exists, select it from the dropdown list.
If the value does not exist, enter the full name, and then select it from the dropdown.
Click Close.
Click the People icon and select the Groups tab.
Select the group you want to edit and select the Settings tab.
In the members section, click Remove to the right of the member you want to remove.
Click Delete to confirm.
Click the People icon and select the Groups tab.
Select the group you want to edit.
Click the more actions icon, and select Delete.
Click Delete to confirm.
Click the People icon and select Users or Groups.
Select the user or group you want to edit and select the Settings tab.
In the Attributes section, click the more actions icon on the attribute value you want to remove.
Click Remove and Confirm.
Using any other attribute in Microsoft Entra ID as a matching attribute results in an error. See the for details about attribute matching and how to configure it.
Alternatively, remove the . Then, trigger an update for that user in Microsoft Entra ID by making a change to any value for that user. Microsoft Entra ID will send an update for that user to Immuta, and Immuta will remove the attribute from the user. Note that if that attribute mapping is ever re-added in Immuta on the app settings page, that attribute will be added to the user again.
See for more details about this limitation.
200
successful operation - user info retrieved successfully
groups
[{"name": "<group_name>"}]
authorizations
{"<authorization_name>": ["<value>"]}
userid
query
The unique user identifier (username in Immuta)
Yes
string
The following options are available when setting up an identity provider that uses the SAML 2.0 protocol.
Allow identity provider initiated single sign on: When enabled, users authenticate once in their identity provider and can log in to Immuta.
Allow identity provider initiated single logout: When enabled, users can log out of Immuta or their identity provider and simultaneously log out of other applications. Additional configuration settings will appear when this checkbox is selected:
Logout URL: The URL of your single sign on application that will be redirected to after you log out of Immuta, as some identity providers differentiate between the logout and authorization URLs.
SLO binding URL: The URL Immuta displays that you can add to your identity provider to specify where to send requests or responses to Immuta's SLO requests.
Encryption private key: An optional private key to encrypt requests.
Decryption private key: The private key for decrypting attribute assertions from the identity provider.
Display name: The internal ID of the identity manager in Immuta. This setting cannot be changed once the configuration is saved.
Entry point: The URL of your single sign on application that the Immuta login page will redirect to.
External groups and attributes endpoint: A REST endpoint that Immuta will use to retrieve a user's groups and attributes.
Issuer: The URL of the identity provider that issues assertions for authentication.
Migrate users: Migrate users from a previously configured identity provider to the current identity provider.
SCIM support: When enabled, your identity provider automatically creates new users in Immuta and updates existing user accounts, whether or not users log in to Immuta. When you click this checkbox, Immuta generates a SCIM API key.
Signing certificate: Your identity provider's public signing certificate.
Sync attributes from SAML to Immuta: Allows attributes added in your identity provider to be synced with Immuta.
Attribute delimiter: The character used to split values in a string of attributes. After enabling sync attributes, providing delimiters for attributes is required.
Attribute prefix: The prefix used for attribute keys.
Sync groups from SAML to Immuta: Allows groups added in your identity provider to be synced with Immuta.
Group attribute: The attribute that contains the user's group. Enable sync groups from SAML to Immuta to make this option available.
User ID attribute: The attribute that contains the user's username.
Immuta policies are dynamic and change for the user accessing data. Every user accessing policy-protected data must exist in Immuta, regardless of if they will interact with the Immuta UI.
Manage personas and permissions: Add, edit, and delete the permissions on your Immuta users.
Use native user impersonation: Enable, grant, and use user impersonation for Azure Synapse Analytics, Databricks, Redshift, Snowflake, or Starburst (Trino).
Manage attributes and groups: Add, edit, and delete user's attributes and groups.
Map user IDs: Ensure policies and audit work correctly by mapping the user's ID from the integration to Immuta.
Configure an external user info endpoint: Configure your IAM in Immuta to retrieve users' groups and attributes from an external HTTP endpoint.
Personas and permissions: This reference guide describes Immuta's permissions and the user personas that they apply to.
Attributes and groups: This reference guide describes attributes and groups in Immuta.
Best practice: Use external and internal IAM
Use an external IAM for authentication and Immuta's internal IAM to manage attributes.
Click the People icon in the navigation and select the Users tab.
Click the New User button.
Fill out the Full Name and Email fields in the dialog. Note: The user's email address will be used as the username and must be unique.
Click the Create button.
Click the People icon in the navigation and select the Users tab.
Select the user you want to edit and select the Settings tab.
Click Add Permissions.
Click the Select Permission dropdown, and select the permission you want to give the user.
Click the People icon in the navigation and select the Users tab.
Select the user you want to disable, and click the more actions icon.
Select Disable User.
Click Disable in the confirmation dialog.
Requirement: USER_ADMIN permission
Note: This action permanently deletes all data associated with this user from Immuta, including data source subscriptions, and a timestamp of this event will be captured in the audit logs. The ability to create governance reports against this user will no longer be possible. This action cannot be undone.
Click the People icon in the navigation and select the Users tab.
Select the user you want to disable, and click the more actions icon.
Select Permanently Delete.
Click Permanently Delete User in the confirmation dialog.
Type Delete to confirm deleting the user permanently.
Click the Confirm Permanent Delete button.
Prerequisite: An IAM configured in Immuta
Click the People icon in the navigation and select the Users tab.
Click the more actions icon and select Migrate User.
Enter their username in the modal that appears and click Migrate User.
Click the People icon in the navigation and select the Users tab.
Select the user you want to edit and select the Settings tab.
Click Remove on the permission you want to remove.
Click the People icon in the navigation and select the Users tab.
Click the Metrics button.
Complete the Number of Days field in the dialog that appears, and then click Download to download the JSON file.
Once an account has been disabled, it will not appear in the list of current Immuta users. To show the disabled accounts,
Click the People icon in the navigation and select the Users tab.
Use Filters to filter the table to Include Accounts and check the Disabled box.
Native impersonation allows users to natively query data as another Immuta user.
User impersonation is supported with
Impersonating users in projects
If you are impersonating a user who is currently in a project, you will only see data sources within that project. For details about this behavior, see the description of project contexts.
Select Enable Impersonation when configuring the Redshift integration on the App Settings page.
After enabling user impersonation with your Amazon Redshift integration, there are two ways to give a user permission to use the feature: in the Immuta UI or in Amazon Redshift. Use the tabs below to select one method.
As an Immuta user with the permission USER_ADMIN,
Click the People icon in the navigation and select the Users tab.
Select the user you want to edit and select the Settings tab.
Click Add Permissions.
Click the Select Permission dropdown, and select the IMPERSONATE_USER permission.
As a Redshift superuser,
Navigate to your Redshift instance.
Run ALTER GROUP <Impersonation Group> ADD USER <Redshift User>.
To impersonate another user in Redshift,
Run CALL immuta_procedures.impersonate_user(<Immuta username of the user to impersonate>).
Run queries.
To end user impersonation in Redshift, run CALL immuta_procedures.impersonate_user(<NULL>).
To revoke permission to impersonate users,
As an Immuta user with the permission USER_ADMIN,
Click the People icon in the navigation and select the Users tab.
Select the user you want to edit and select the Settings tab.
Click Add Permissions.
Click the Select Permission dropdown, and select the IMPERSONATE_USER permission.
As a Redshift superuser,
Navigate to your Redshift instance.
Run ALTER GROUP <Impersonation Group> DROP USER <Redshift User>.
User impersonation is specific to the script and session in which it was set. Using a new script or running a subset of script queries without setting the context will result in the queries being run as the regular user.
Select Enable Impersonation when configuring the Synapse Analytics integration on the App Settings page.
After enabling user impersonation with your Azure Synapse Analytics integration, there are two ways to give a user permission to use the feature: in the Immuta UI or in Azure Synapse Analytics. Use the tabs below to select one method.
As an Immuta user with the permission USER_ADMIN,
Click the People icon in the navigation and select the Users tab.
Select the user you want to edit and select the Settings tab.
Click Add Permissions.
Click the Select Permission dropdown, and select the IMPERSONATE_USER permission.
As a Synapse user,
Navigate to your Synapse instance.
Run EXEC sp_addrolemember N'<Impersonation Role>', N'<Synapse User>'.
To impersonate another user in Synapse,
Run the following command:
Run queries.
To end user impersonation in Synapse, run EXEC sys.sp_set_session_context @key = N'NULL', @value = '<NULL>'.
To revoke permission to impersonate users,
As an Immuta user with the permission USER_ADMIN,
Click the People icon in the navigation and select the Users tab.
Select the user you want to edit and select the Settings tab.
Click Remove for the IMPERSONATE_USER permission.
As a Synapse user,
Navigate to your Synapse.
Run EXEC sp_droprolemember N'<Impersonation Role>', N'<Synapse User>'.
User impersonation is specific to the script and session in which it was set. Opening a new script will revert the user back to themselves.
Scala Clusters
Immuta discourages use of this feature with Scala clusters, as the proper security mechanisms were not built to account for user isolation limitations in Scala clusters. Instead, this feature was developed for the BI tool use case in which service accounts connecting to the Databricks cluster need to impersonate Immuta users so that policies can be enforced.
Databricks user impersonation allows a Databricks user to impersonate an Immuta user. With this feature,
the Immuta user who is being impersonated does not have to have a Databricks account, but they must have an Immuta account.
the Databricks user who is impersonating an Immuta user does not have to be associated with Immuta. For example, this could be a service account.
When acting under impersonation, the Databricks user loses their privileged access, so they can only access the tables the Immuta user has access to and only perform DDL commands when that user is acting under an allowed circumstance (such as workspaces, scratch paths, or non-Immuta reads/writes).
Follow one of these methods to allow specified Databricks users to impersonate Immuta users:
In the cluster policy JSON in the Immuta UI, add a comma-separated list of Databricks users who are allowed to impersonate Immuta users for the IMMUTA_SPARK_DATABRICKS_ALLOWED_IMPERSONATION_USERS Spark environment variable.
In the Spark environment variables section of the Databricks UI, add IMMUTA_SPARK_DATABRICKS_ALLOWED_IMPERSONATION_USERS followed by a comma-separated list of Databricks users who are allowed to impersonate Immuta users.
Prevent Users from Changing Impersonation User in a Given Session
If your BI tool or other service allows users to submit arbitrary SQL or issue SET commands, set IMMUTA_SPARK_DATABRICKS_SINGLE_IMPERSONATION_USER to true to prevent users from changing their impersonation user once it has been set for a given Spark session.
Once the cluster is configured with a list of Databricks users who are allowed to impersonate Immuta users, run the following SQL command to set the user you want to impersonate:
This command generates an API token for the specified user that queries Immuta for metadata pertinent to that user. When generating the token, the impersonated username is matched with the corresponding IAM user. The IAM used by default is the built-in IAM in Immuta, but can be set using the IMMUTA_USER_MAPPING_IAMID environment variable.
Run queries as the impersonated Immuta user:
Once impersonation is active, any query issued in the session will have the appropriate data and subscription policies applied for the impersonated user. Consider the example queries in the tabs below.
Without User Impersonation
Policies on this data source mask sensitive values unless users possess a specified attribute.
If the user querying the data possesses that attribute, they can see the unmasked values.
With User Impersonation
Policies on this data source mask sensitive values unless users possess a specified attribute.
If the user queries the data source impersonating an Immuta user (smwilliams@example.com) who does not possess that attribute, the sensitive data is masked.
Audited queries include an impersonationUser field, which identifies the Databricks user impersonating the Immuta user:
To end user impersonation for the session, run
The only way to enable this feature is through cluster configuration. The IMPERSONATE_USER permission in Immuta will not allow a user to perform native impersonation in Databricks.
User impersonation is automatically enabled with your Starburst (Trino) integration, but the authenticated user must be given the IMPERSONATE_USER permission in Immuta or match the Starburst (Trino) immuta.user.admin regex configuration property.
To grant the user IMPERSONATE_USER permission, as an Immuta user with the permission USER_ADMIN,
Navigate to your Immuta homepage.
Click the People icon and select Users in the left sidebar. Then select the user.
Click Add Permissions.
Click the Select Permission dropdown, and select the IMPERSONATE_USER permission.
Click Close.
The Starburst (Trino) integration supports the native Starburst or Trino impersonation approaches:
JDBC method: In your JDBC connection driver properties, set the sessionUser property to the Immuta user you want to impersonate. See the Starburst JDBC driver documentation for details.
Trino CLI method: Set the --session-user property to specify the session user as the Immuta user you want to impersonate when invoking the Trino CLI. See the Starburst release notes for details.
To view the user you are impersonating, run SHOW SESSION like 'immuta.immuta_user'.
To end user impersonation, run RESET SESSION immuta.immuta_user.
To revoke permission to impersonate users, as an Immuta user with the permission USER_ADMIN,
Click the People icon in the navigation and select the Users tab.
Select the user you want to edit and select the Settings tab.
Click Remove for the IMPERSONATE_USER permission.
The user's permissions to impersonate users are not checked until the query is run. If the user does not have the IMPERSONATE_USER permission in Immuta, they will be able to run the command to impersonate a role, but will not be able to query as that role.
Select Enable Impersonation when configuring the Snowflake integration on the App Settings page.
After enabling user impersonation with your Snowflake integration, there are two ways to give a user permission to use the feature: in the Immuta UI or in Snowflake. Use the tabs below to select one method.
As an Immuta user with the permission USER_ADMIN,
Click the People icon in the navigation and select the Users tab.
Select the user you want to edit and select the Settings tab.
Click Add Permissions.
Click the Select Permission dropdown, and select the IMPERSONATE_USER permission.
As a Snowflake user with the ACCOUNTADMIN role,
Navigate to your Snowflake instance.
In a worksheet run GRANT ROLE <<Impersonation_Role>> TO USER "<<Snowflake User>>".
In this example, the Impersonation Role is the name entered on the Immuta App Settings page when the feature was enabled. The default is IMMUTA_IMPERSONATION, but the admin may have customized it. The Snowflake User is the username of the Snowflake user that will now have permission to impersonate other users.
To impersonate another user in Snowflake,
Open a New Worksheet and set your role to the impersonation role specific to your organization.
Run SET immuta_user = '<<Immuta username of the user to impersonate>>'.
Run queries within that worksheet.
To revoke permission to impersonate users,
As an Immuta user with the permission USER_ADMIN,
Click the People icon in the navigation and select the Users tab.
Select the user you want to edit and select the Settings tab.
Click Remove for the IMPERSONATE_USER permission.
As a Snowflake user with the ACCOUNTADMIN role,
Navigate to your Snowflake instance.
In a worksheet run REVOKE ROLE <<Impersonation Role>> FROM USER "<<Snowflake User>>".
In this example, the Impersonation Role is the name entered on the Immuta App Settings page when the feature was enabled. The default is IMMUTA_IMPERSONATION, but the admin may have customized it. The Snowflake User is the username of the Snowflake user that will now have permission to impersonate other users.
Native impersonation is specific to the workspace and session in which it was set. Opening a new worksheet will revert the user back to themselves.
Snowflake auditing will show the user running the queries as the user logged in to Snowflake not as the user they are impersonating.
Permissions are a system-level mechanism that control what actions a user is allowed to take through the Immuta API and UI and reflect their user persona. Permissions can be added to any user by a user admin, but the permissions themselves are managed by Immuta and cannot be added or removed in the Immuta UI.
Application admins: Application admins manage the configuration of Immuta for their organization. These users can configure Immuta to use external identity managers and catalogs, enable or disable data handlers, adjust email and cache settings, generate system API keys, and manage various other advanced settings.
Auditors: Auditors can see and inspect all audit logs associated with Immuta and its integrations. This includes query, authentication, policy, project, and tag events from your Immuta users and data sources.
Data owners: In order for data to be available in the Immuta platform, a data owner — the individual or team responsible for the data — needs to connect their data to Immuta. Once data is connected to Immuta, that data is called a data source. Once registered as a data source, the data owners have permission to set subscription policies and data policies on those data sources. Data owners can also build global policies just like governors, but they are restricted to only the data sources they own.
Data users: Data users consume the data available through Immuta in their data platform as usual.
Domain delegates: These users accountable to manage actions on data sources in a particular domain. This currently includes applying policies and auditing activity.
Governors: Governors set global policies within Immuta, meaning they can apply policies across all data sources. Additionally they can leverage Detect, manage all tags, and manage all purposes.
Project managers: These users inspect, manage, approve, and deny various project changes, including purpose requests and project data sources.
Project owners: These users can create their own project to get approvals for purpose-based access controls (PBAC).
User admins: These users are able to manage the permissions, attributes, and groups that attach to each user. Permissions are only managed locally within Immuta, but groups and attributes can be managed locally or derived from user management frameworks, such as LDAP or Active Directory, that are external to Immuta.
The table below illustrates the global and domain permissions associated with each user persona.
APPLICATION_ADMIN
Global
Application admin
Gives the user access to administrative actions for the configuration of Immuta. These actions include configuring integrations, adding external IAMs, and connecting external catalogs.
AUDIT
Global
Auditor
Gives the user access to the audit logs
Audit Activity
Domain delegate
Audit domain-related activity within particular domain(s)
CREATE_DATA_SOURCE
Global
Create data sources
CREATE_DATA_SOURCE_IN_PROJECT
Global
CREATE_FILTER
Global
N/A
Create and save a search filter (This permission has been deprecated.)
CREATE_PROJECT
Global
Project owner
Create and manage projects
FETCH_POLICY_INFO
Global
Data owner
Granted access to an endpoint that returns visibilities, masking information, and filters for a given data source
GOVERNANCE
Global
Governor
Create and manage purposes
Create and manage tags
Create global policies that apply to any data sources (inside or outside domains)
Create, manage, and delete domains (domain must be empty to be deleted)
Add existing data sources to any domain
Remove data sources from any domain without adding it to another domain
IMPERSONATE_USER
Global
Data user
Impersonate other Immuta users
Manage Policies
Domain delegate
Create policies that apply to the domain(s) they are authorized to
PROJECT_MANAGEMENT
Global
Project manager
Create purposes, approve and deny purpose requests, and manage project data sources
USER_ADMIN
Global
User admin
Manage user permissions, including domain-specific permissions on all domains
You can also create custom permissions, which should be used for assigning manual subscription policy approvals.
There are several roles that can be assigned to users and groups for a specific data source. See the Data sources in Immuta page for a list of data source roles and descriptions.
Collecting Immuta usage metrics from customers helps Immuta gain insight into how customers are using Immuta (not who they are or what their data looks like) to understand what features are heavily used. These metrics guide improvements to the user experience.
The metrics collected are anonymized data points that provide information on Immuta feature usage but cannot be linked to an individual user or data source. Specifically, Immuta collects what workflows the users are completing and what the users are touching in the UI.
Workflows users are completing: These workflow metrics (creating policies, data sources, projects, etc.) are aggregates, such as the number of data sources created in a day, not individual events.
What users are touching: These metrics indicate what users click in Immuta, such as the create a data source button.
Product input: Input from customer metrics helps Immuta make product decisions. Providing your metrics is the best way to provide product feedback directly to Immuta.
Improve user experience: Insights into the activity of different personas (governors, data owners) can be used to improve the Immuta user interface and create meaningful feedback loops.
Internal insights: Gaining insights into your own Immuta use can reveal habit loops or pain points that users experience that may not be obvious. Metrics will enable those to be identified and improved.
Prove value: Quantifying the areas of Immuta that you are using the most is the key to understanding the value that Immuta brings to your organization.
within a project (This permission has been deprecated.)