Write a Global Data Policy
Use Case
Compliance Requirement: Redact all personal information for everyone except when running queries in Test and Prod.
For this organization's purposes, they should write a Global Policy that masks all personal information, except for system accounts running queries in Test and Prod. To do so, they will use the tags and attributes previously created to build their Global Data Policy. The steps below use this scenario to illustrate the policy, but other policy builder options are noted throughout the tutorial.
1 - Create a Global Data Policy
Best Practice: Write Global Policies
Build Global Policies with tags instead of writing Local Policies to manage data access. This practice will prevent you from having to write/re-write single policies for every data source added to Immuta.
- Click the Policies page icon in the left sidebar and select the Data Policies tab at the top of this page.
-
Click Add Policy, enter a name for your policy, and then select Mask from the first dropdown menu.
-
Select columns tagged and then select PII from the subsequent dropdown menu. Additional options include columns with any tag, columns with no tags, all columns, or columns with names spelled like.
-
Select using hashing from the next dropdown menu. Additional custom masking types include with reversibility, by making null, using a constant, using a regex, by rounding, with format preserving masking, with K-Anonymization, using randomized response, or using the custom function. Click on the tabs below to view specific instructions for these masking policies:
using a constant
Enter a constant in the field that appears next to the masking type dropdown.
by rounding
- Select using fingerprint or specifying the bucket from the subsequent dropdown menu.
- If specifying the bucket, select the Bucket Type and then enter the bucket size.
Note: If you choose by rounding as your masking type, the statistics of the data fingerprint will autogenerate the bucket size when the policy is applied to a data source.
using a regex
- Enter a regular expression and replacement value in the fields that appear next to the masking type dropdown.
- From the next dropdown, choose to make the regex Case Insensitive and/or Global.
with K-Anonymization
Select either using fingerprint or requiring group size of at least and enter a group size in the subsequent dropdown menu.
using the custom function
Enter the custom function native to the underlying database.
Note: The function must be valid for the data type of the column. If it is not, the default masking type will be applied to the column.
-
Select everyone except from the next dropdown menu to continue the condition. Additional options include everyone and everyone who.
-
In the subsequent dropdown menus, choose possesses attribute and select Environment dev, or, and Environment prod. You could also use group or purpose to complete a condition.
Notes:
-
If you choose for everyone who as a condition, complete the Otherwise clause before continuing to the next step.
-
You can add more than one condition by selecting + ADD. The dropdown menu in the far right of the Policy Builder contains conjunctions for your policy. If you select or, only one of your conditions must apply to a user for them to see the data. If you select and, all of the conditions must apply.
-
-
Opt to complete the Enter Rationale for Policy (Optional) field, and then click Add.
-
The dropdown menu beneath Where should this policy be applied should already be complete. However, you have the option to select On all data sources or On data sources. If you selected On data sources, finish the condition in one of the following ways:
tagged
Select this option and then search for tags in the subsequent dropdown menu.
with columns tagged
Select this option and then search for tags in the subsequent dropdown menu.
with column names spelled like
Select this option, and then enter a regex and choose a modifier in the subsequent fields.
in server
Select this option and then choose a server from the subsequent dropdown menu to apply the policy to data sources that share this connection string.
created between
Select this option and then choose a start date and an end date in the subsequent dropdown menus.
-
Click Create Policy, and then click Activate Policy or Stage Policy.
2 - Create a Custom Certification
-
Click Add Certification in the top right corner of the Data Policy Builder.
-
Enter a Certification Label and Certification Text in the corresponding fields of the dialog that appears.
-
Click Save.
Results
Now that this Global Policy is active, users with the attribute Environment.dev will see redacted data and users with
the attributes Environment.test or Environment.prod will see all the data:
Dev User
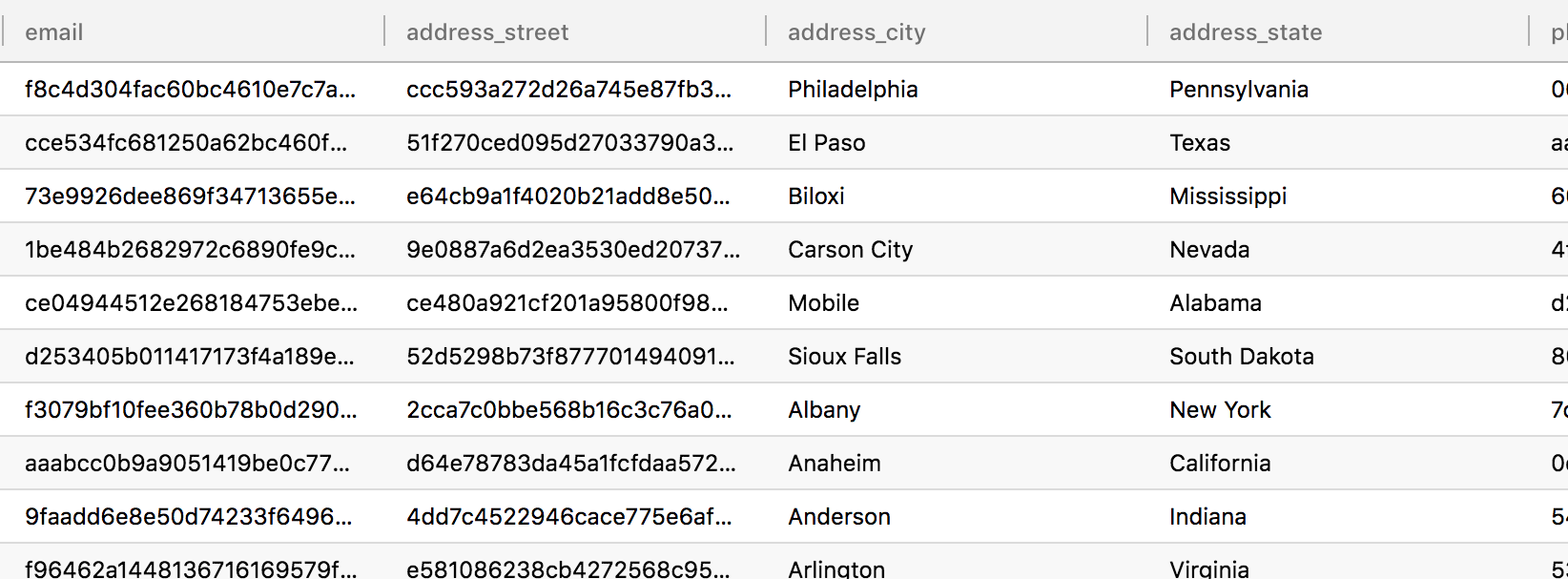
Test User
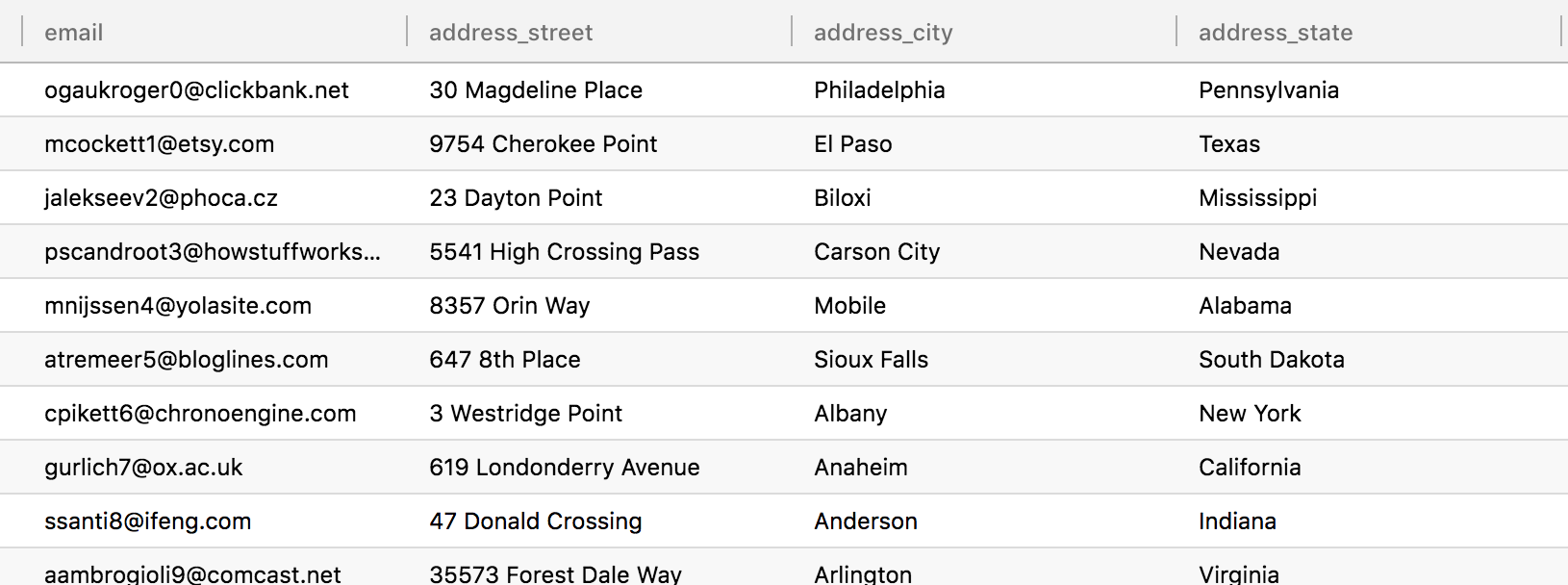
Prod User
